
physical - How does full memory encryption in newer processes protect against DMA attacks? - Information Security Stack Exchange

VeraCrypt / Forums / General Discussion: Elcomsoft Breaks the Latest Version of VeraCrypt (3 June, 2021)

Amazon.com: SparkFun Thing Plus - ESP32-S2 WROOM - Highly-Integrated Feather Form-Factor Development Board Equipped w/ a 2.4 GHz WiFi System-on-Chip (SoC) - Transparent External Flash & RAM encryption : Electronics


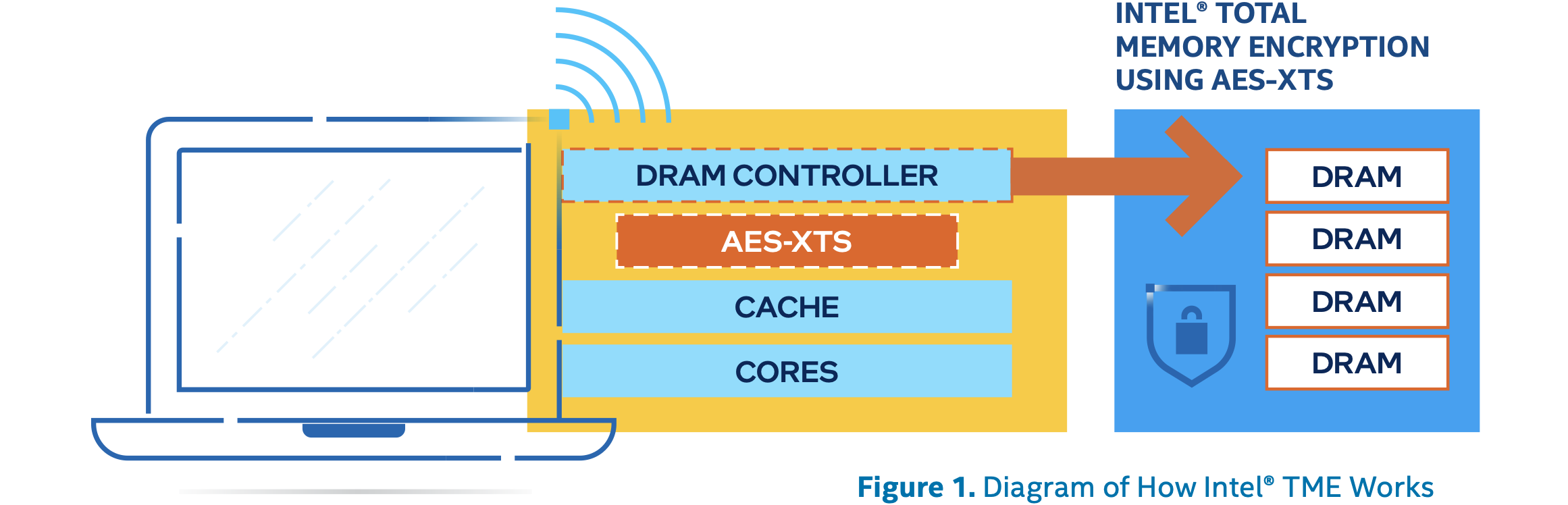
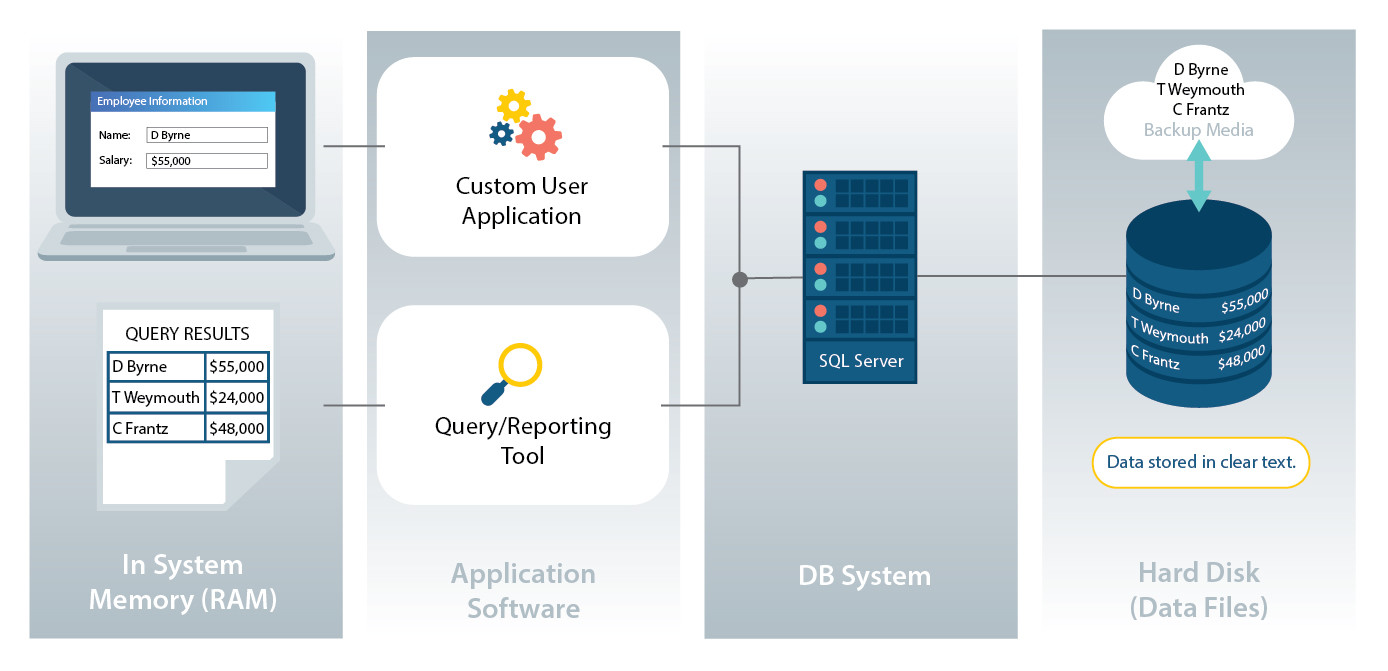
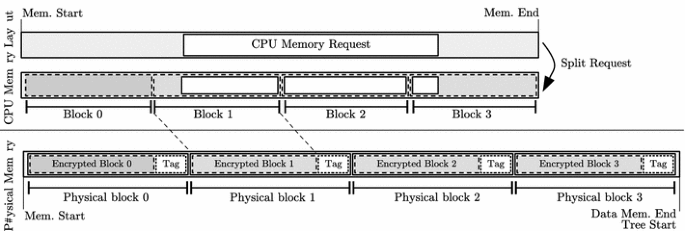
![PDF] A Memory Encryption Engine Suitable for General Purpose Processors | Semantic Scholar PDF] A Memory Encryption Engine Suitable for General Purpose Processors | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/978b079e957c62dcfe3bf3cf2d944ec05b97f8d1/5-Figure2-1.png)

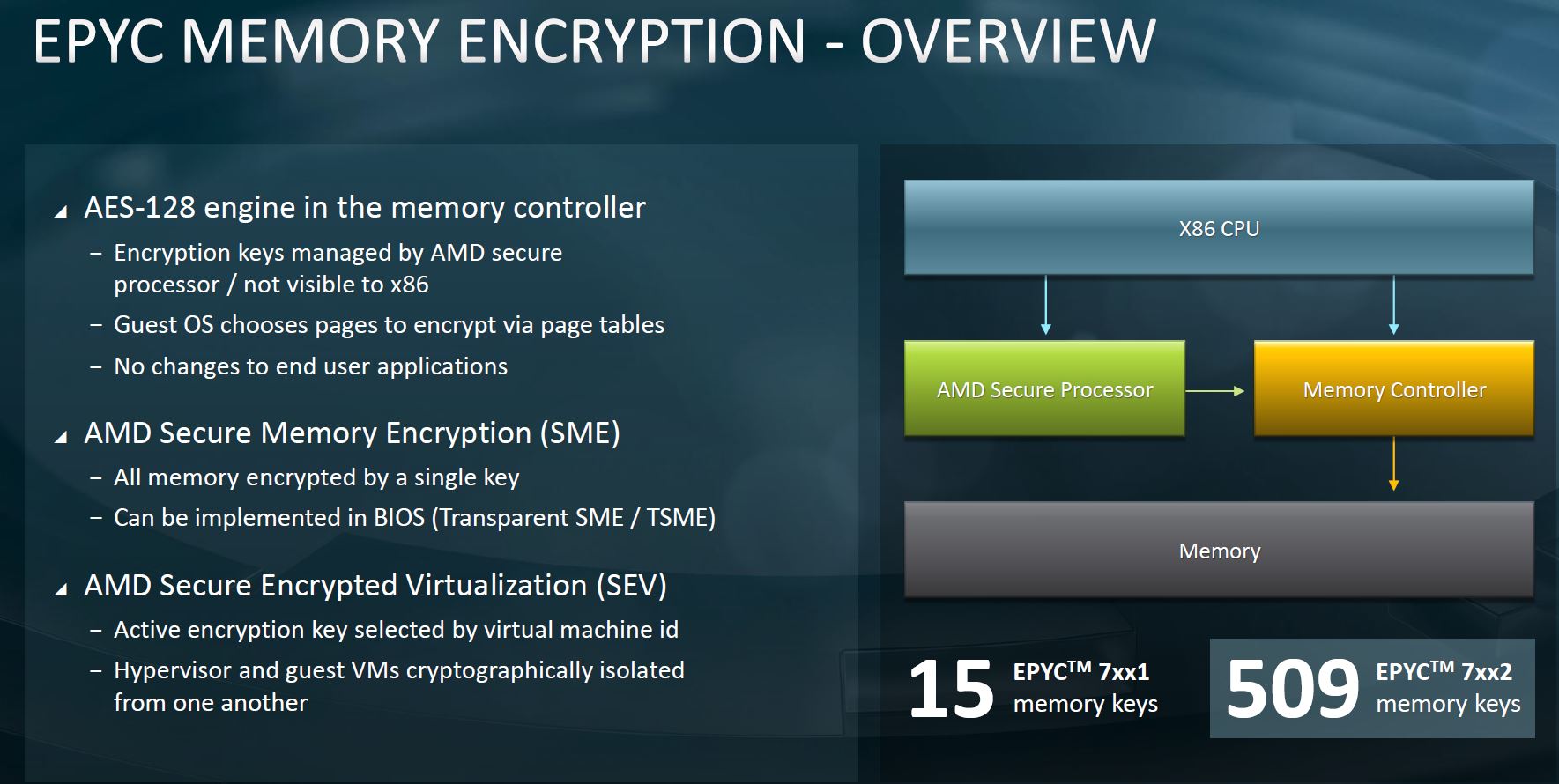




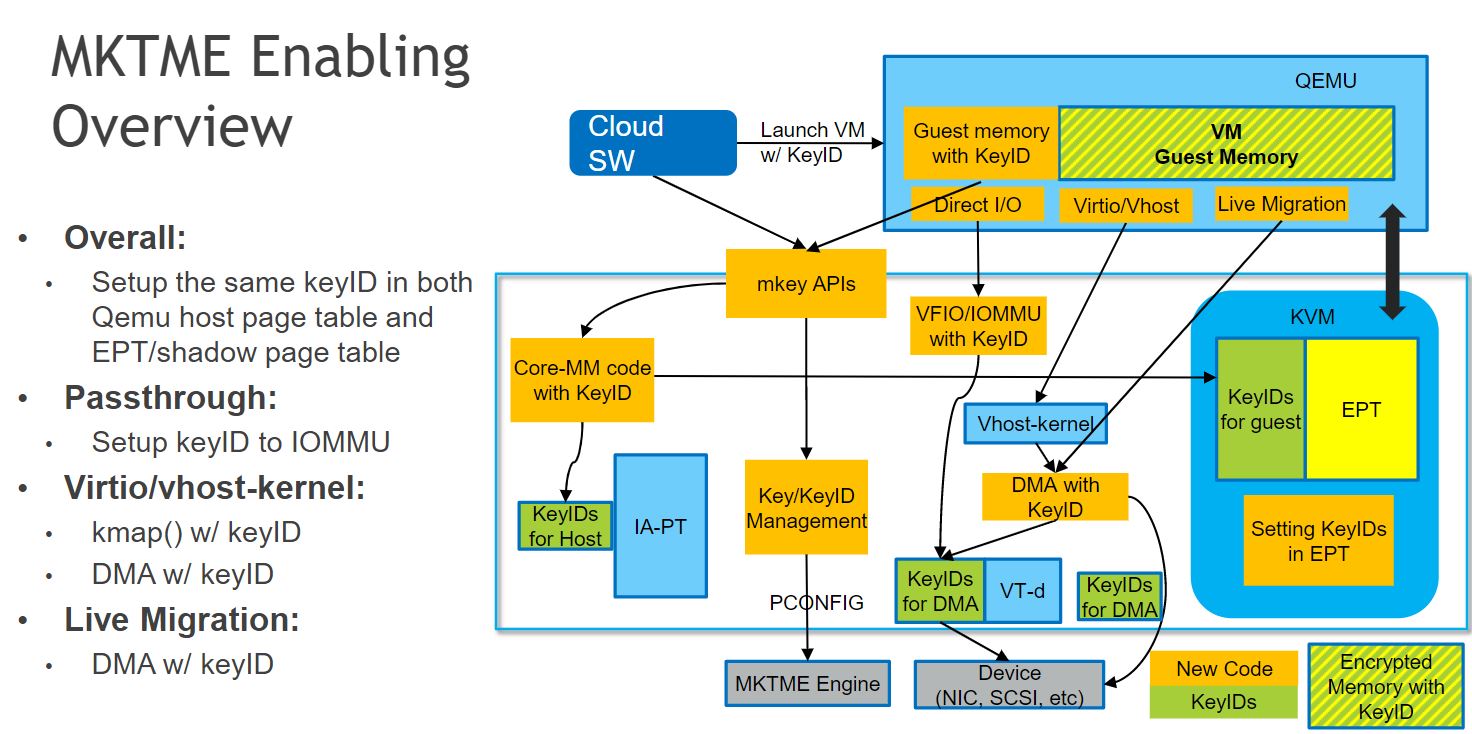

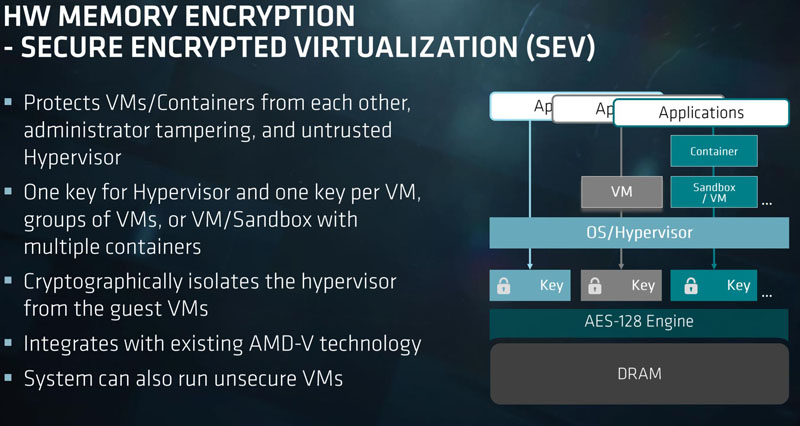

![PDF] A Memory Encryption Engine Suitable for General Purpose Processors | Semantic Scholar PDF] A Memory Encryption Engine Suitable for General Purpose Processors | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/978b079e957c62dcfe3bf3cf2d944ec05b97f8d1/3-Figure1-1.png)

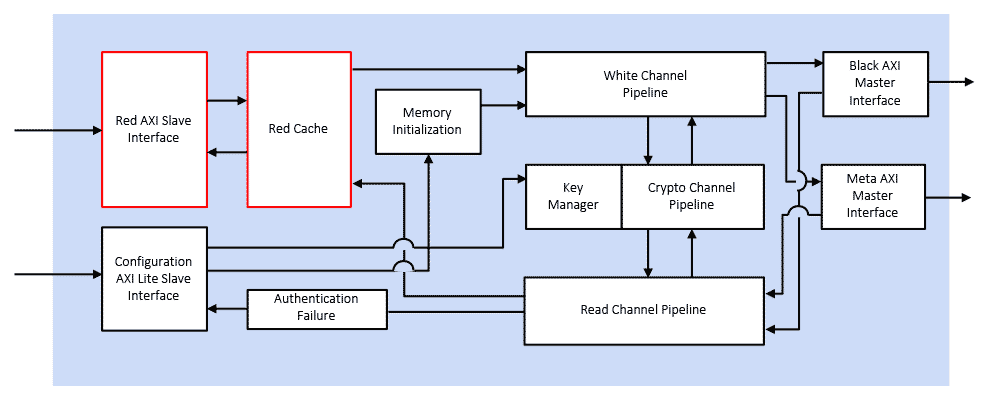
![PDF] RAM is Key Extracting Disk Encryption Keys From Volatile Memory | Semantic Scholar PDF] RAM is Key Extracting Disk Encryption Keys From Volatile Memory | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/86a28a5f04772c2fff73b7b067bdef0e4e8cf811/14-Figure5-1.png)